Simple and secure IT integration of external service providers
Facilitate uncomplicated and protected information exchange

“CIOs want to transform IT from reactive contractors to trusted, competitive providers of business-centric IT services that deliver greater value.”
Use the Service-Optimizing IT Operating Model to Become a Business-Centric Provider of IT Services, Gartner, 2022
IT environment for external service providers
In the modern business world, external service providers are often an important part of the value chain. The challenge is to provide them with efficient and standardised access to the corporate resources they need without compromising security.
Challenges of traditional IT
- The provision of secure access requires different technological approaches and interfaces, especially if external service providers work with differing technological requirements.
- Sharing applications, files and documents requires coordination processes if the involved parties use other systems and formats.
- Checking whether external service providers adhere to the applicable compliance and security standards can lead to time-consuming audit processes.
IT integration of external service providers with oneclick™
Discover the benefits of the oneclick™ digital workplaces for external service providers:
Structured separation of IT environments
Use our platform and portal approach to ensure a clear separation between the in-house IT landscape and systems of external service providers.
Access right control
Set individual access rights to meet your security requirements and the functional needs of your external service providers.
Auditable compliance
Document user activity with detailed access logs and ensure compliance policies are followed.
Scalable infrastructure
Use the flexibility of our cloud solution to quickly scale IT resources according to the requirements of projects and the number of external service providers.
Easy administration and onboarding
Simplify the administration process and speed up onboarding of new service providers with an intuitive user interface that enables centralised management.
Examples of use
Workday
before
A company hires an external call center with its own CRM system for customer care.
- Lengthy application audit and dedicated development of interfaces
with oneclick™
Access to a tested working environment that is directly linked to the in-house CRM system and also includes the telephony solution and tools for data analysis.
- Information exchange via existing multi-interface
A company hires an external call center with its own CRM system for customer care.
- Lengthy application audit and dedicated development of interfaces
Access to a tested working environment that is directly linked to the in-house CRM system and also includes the telephony solution as well as tools for data analysis.
- Information exchange via existing multi-interface
Workday
before
A consulting firm needs access to confidential financial data for a strategy analysis and must use special software for this.
- Elaborate permit procedures and access organisation
with oneclick™
Advisors can securely access the desired applications and data via the oneclick™ Platform.
- Already established trust position
A consulting firm needs access to confidential financial data for a strategy analysis and must use special software for this.
- Elaborate permit procedures and access organisation
Advisors can securely access the desired applications and data via the oneclick™ Platform.
- Already established trust position
Workday
before
External developers have to install and configure software and libraries every time they receive a new job.
- Waste of time and resources
with oneclick™
The company can provide pre-configured working environments that contain all necessary components.
- More efficient cooperation
External developers have to install and configure software and libraries every time they receive a new task from their contractor.
- Waste of time and resources
The contractor can provide pre-configured working environments that contain all necessary components.
- More efficient cooperation
oneclick™ technology highlight for IT integration of external service providers
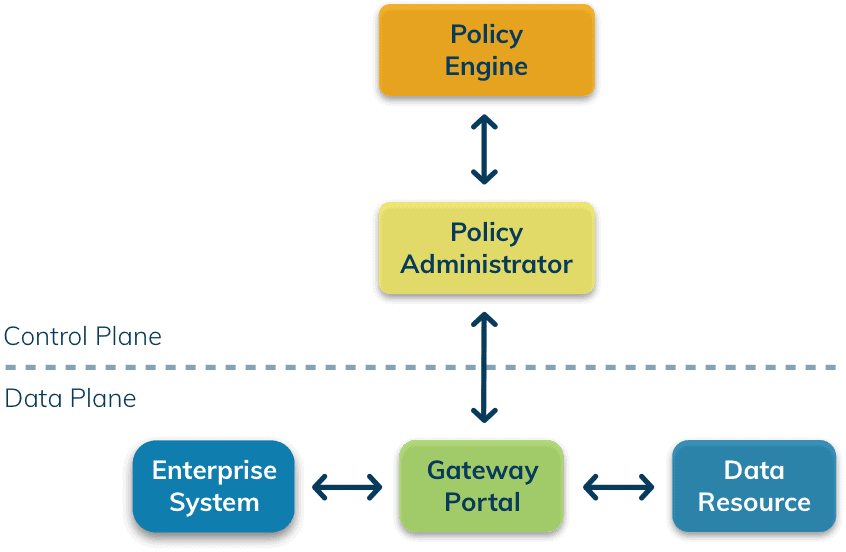
Zero Trust Architecture (ZTA)
The Zero Trust Architecture (ZTA) of oneclick™ treats every user equally, regardless of whether they are internal employees or external partners. Individuals are only granted access to specific company resources via gateway portal and not to entire network segments. Authentication and authorisation are checked continuously.
Choose between six solutions, depending on your requirements
Particularly suitable for …
- an immediate demand
- rather constant users
- low own IT resources
For fast and affordable deployment of software to a smaller user number on a single virtual machine in your Public Cloud.
Particularly suitable for …
- larger user numbers
- the requirement for adaptable costs
- interest in IT outsourcing
For cost-effective and flexible operation of a client desktop infrastructure on a scalable pool of virtual machines in your and other Public Clouds.
Particularly suitable for …
- decentralized workforce
- the need to create new workplaces quickly
- data worth protecting
For the central and secure provision of virtual desktops and virtualized applications on a self-managed infrastructure.
Particularly suitable for …
- underutilized physical servers
- the desire to save costs and energy consumption
- high requirements for availability
For efficient creation and management of virtual machines on bare metal servers, either on-premises or in a Private Cloud.
Particularly suitable for …
- seasonal user fluctuations
- short-term peak loads
- limited on-premises capacities
For uncomplicated load balancing into your Public Cloud when customers no longer have any on-premises capacities available.

Particularly suitable for …
- reliable protection of web apps
- encryption of communication
- load balancing and fail-safety
Secure Web App Deployment
For ensuring that no user or client communicates directly with the web server, maintaining its anonymity.
Would you like personal advice on the topic of simple and secure IT integration of external service providers?
Contact us and one of our consultants will get in touch with you shortly.